While the digital age has ushered in a variety of technical remedies, Trojan Horse Email Example remain a classic and sensible device for various facets of our lives. The responsive experience of connecting with these templates gives a feeling of control and company that enhances our busy, digital presence. From improving performance to assisting in creative pursuits, Trojan Horse Email Example remain to verify that in some cases, the most basic options are the most effective.
How Do You Email A Picture From Your Computer Profile Picture
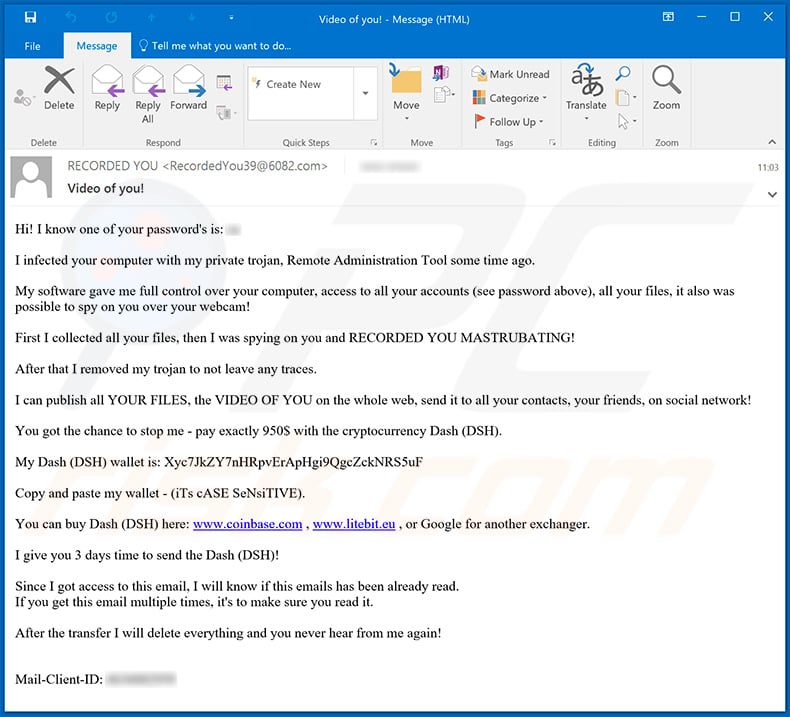
Trojan Horse Email Example
The Your system has been hacked with a Trojan virus scam is a malicious and deceptive email scheme designed to prey on the fears and vulnerabilities of unsuspecting internet users
Trojan Horse Email Example also locate applications in health and wellness and wellness. Fitness organizers, meal trackers, and rest logs are just a couple of instances of templates that can contribute to a much healthier way of life. The act of literally completing these templates can instill a sense of commitment and self-control in adhering to individual health and wellness goals.
Toll Adjustment Reminder With Trojan Horse Codedocu de Blog

Toll Adjustment Reminder With Trojan Horse Codedocu de Blog
For example a user might receive an email from someone they know which includes an attachment that also looks legitimate However the attachment contains malicious code that
Musicians, writers, and designers commonly turn to Trojan Horse Email Example to jumpstart their imaginative projects. Whether it's laying out ideas, storyboarding, or planning a design layout, having a physical template can be a valuable beginning factor. The adaptability of Trojan Horse Email Example permits designers to repeat and refine their work up until they accomplish the preferred outcome.
How To Program A Trojan Horse Mastervalley
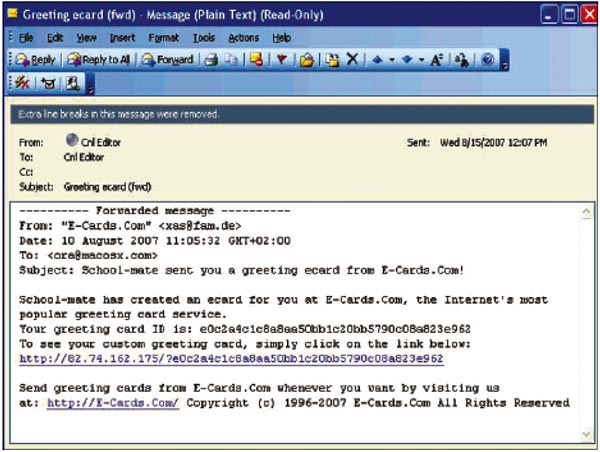
How To Program A Trojan Horse Mastervalley
Email Trojans for example use social engineering tactics to resemble harmless email attachments fooling the user into opening the attached file A Trojan malware infected machine can also transfer it to other systems
In the professional realm, Trojan Horse Email Example use an effective means to manage jobs and jobs. From company strategies and project timelines to billings and cost trackers, these templates simplify important business procedures. Additionally, they give a substantial record that can be conveniently referenced during meetings and discussions.
Is Email Your Trojan Horse To Web Personalization

Is Email Your Trojan Horse To Web Personalization
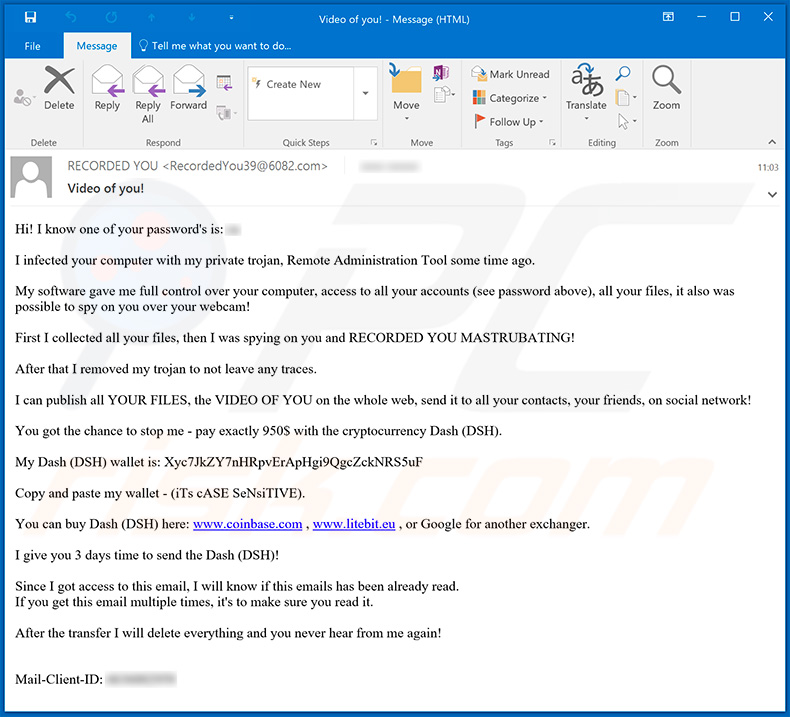
One example may be a backdoor installed unnoticed on the computer via an infected email attachment This gateway ensures that further malware is loaded onto the PC secretly and silently without being noticed
Trojan Horse Email Example are commonly used in educational settings. Teachers commonly count on them for lesson plans, classroom tasks, and grading sheets. Pupils, also, can benefit from templates for note-taking, research study routines, and job planning. The physical visibility of these templates can improve involvement and work as concrete help in the knowing procedure.
Get More Trojan Horse Email Example

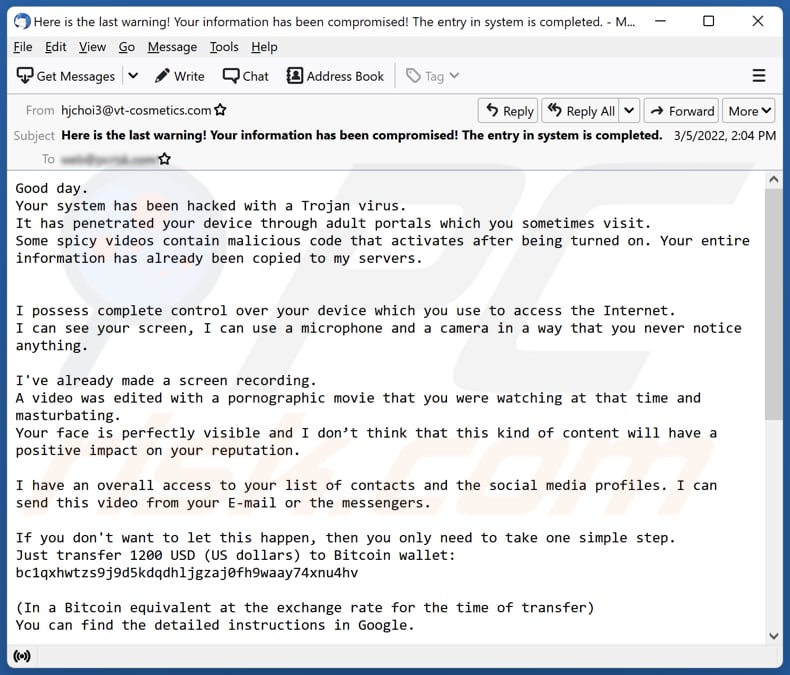


https://malwaretips.com/blogs/your-sys…
The Your system has been hacked with a Trojan virus scam is a malicious and deceptive email scheme designed to prey on the fears and vulnerabilities of unsuspecting internet users

https://www.fortinet.com/resources/cyberglossary/trojan-horse-virus
For example a user might receive an email from someone they know which includes an attachment that also looks legitimate However the attachment contains malicious code that
The Your system has been hacked with a Trojan virus scam is a malicious and deceptive email scheme designed to prey on the fears and vulnerabilities of unsuspecting internet users
For example a user might receive an email from someone they know which includes an attachment that also looks legitimate However the attachment contains malicious code that

The Trojan Horse In The Proposed NEPA Revisions Ocean Noise

Charity Digital Topics What Is Trojan Horse Malware

The G20 s Principles On Institutional Investment A Trojan Horse For

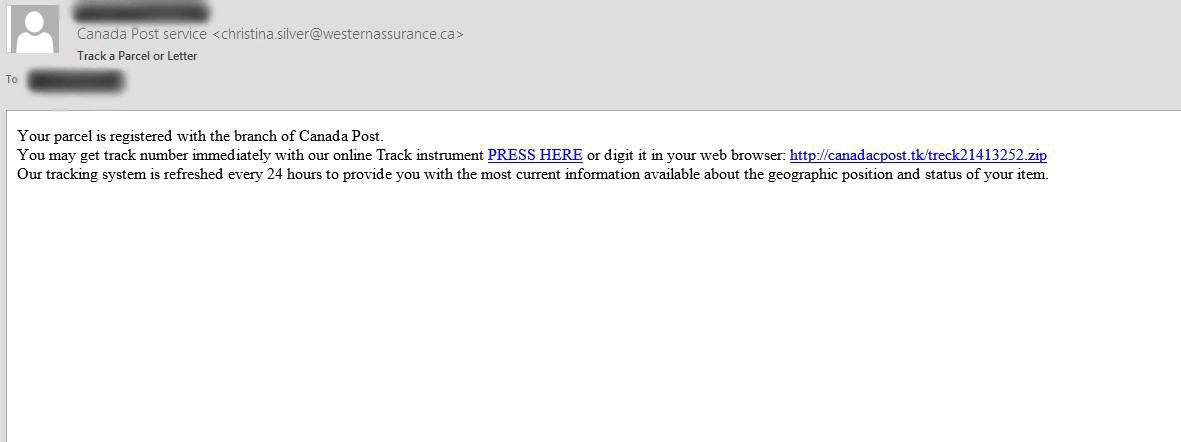
Remove Ursnif Trojan Horse Purolator Phishing Scam
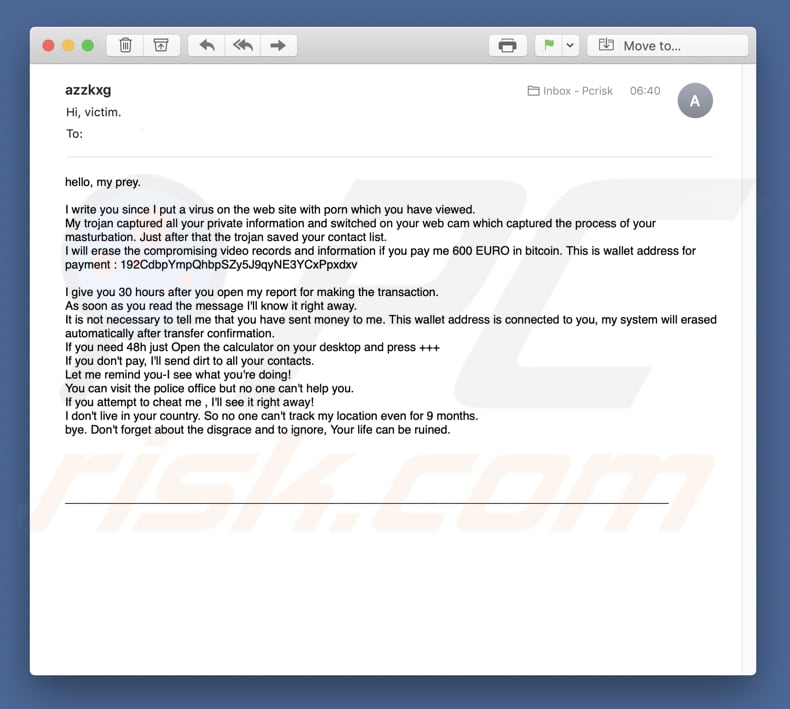
Mein Trojaner Hat Alle Ihre Privaten Informationen Erfasst E Mail
Trojan Virus Popup Apple Community
Trojan Virus Popup Apple Community

TROJAN HORSE LIGHTERSIDE